Securing Mobile Cyber-Physical Systems (CPSs) Against Stealthy Attacks
Overview
As Cyber-Physical Systems (CPSs) employing mobile nodes continue to integrate into the physical world, ensuring their safety and security become crucial goals. Due to their mobility, real-time, energy and safety constraints, coupled by their reliance on communication mediums that are subject to interference and intentional jamming, the projected complexities in Mobile CPSs will far exceed those of traditional computing systems. Such increase in complexity widens the malicious opportunities for adversaries and with many components interacting together, distinguishing between normal and abnormal behaviors becomes quite challenging.
The research work in this project aims to identify new classes of attacks specially stealthy ones that are likely to appear in the near future, and to develop the proper defense mechanisms to prevent, detect and mitigate them. The project is focused on autonomous robotics (e.g., robot swarms) and intelligent transportation systems (e.g., vehicular networks).
Sample Projects
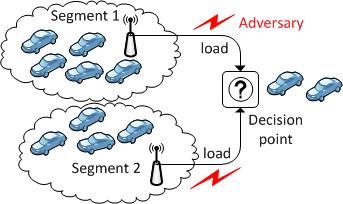
Stuck in Traffic (Sit) Attacks on Intelligent Transportation Systems In this project, we investigate vulnerabilities in systems that rely on wireless communication to optimize traffic through smart traffic signs. We envision vehicular networks in which traffic signs reflect admission ratios to road segments based on load estimates on those segments. The load estimates are obtained through wireless signals from vehicles to the infrastructure (e.g., Road Side Units), with the potential of interference by adversaries. Through instantiating the MDP framework, we expose classes of stealthy attacks - which we term Stuck in Traffic (SiT) attacks -- that aim to cause congestion by exploiting how drivers make decisions when choosing between alternate routes. While the generated policies are suboptimal, they outperform other attack policies such as myopic, random and DoS attacks. |
 |
|
Stealthy Attacks on Multi-agent Systems In multi-agent systems (e.g., swarm robotics), mobile nodes rely on communication to organize themselves and cooperate to achieve common goals. The goal of this project is to develop a general understanding of the impact of interference in communication on the overall behavior of the swarm. In particular, when agents fail to exchange critical information, adverse effects occur since the agents work more independently. A particular instantiation of this project is done on pheromone swarming methods that are used in reconnaissance, surveillance, and search missions in military operations. |
 |
|
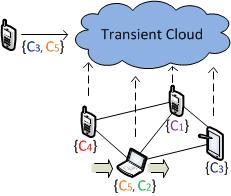
Transient Mobile Clouds Mobile devices are evolving into powerful systems due to recent advances in their communication, storage and computation technologies. They are posed to play a key role in providing a rich collaborative computing platform for various applications. This projects develops "Transient Clouds" -- a collaborative computing platform that allows nearby devices to form an ad-hoc network and provide various capabilities as a cloud service. Transient clouds utilize the collective capabilities of the devices present, along with their social and context awareness that cannot be provided efficiently by the traditional cloud. We envision Transient Clouds to be utilized in temporal scenarios in which the cloud is created by the devices present in an environment and would disappear as the devices leave the network. In this project, we develop various assignment algorithms for assigning tasks to devices to ensure the security, privacy and integrity of the computation and the data. Our methods are evaluated through simulation and real implementation on the Android platform (using the newly introduced Wi-Fi Direct framework). |
 |
Publications:
- Ahmed Anwar, George Atia and Mina Guirguis "Adaptive Topologies Against Jamming Attacks in Wireless Networks: A Game-Theoretic Approach". The Elsevier International Journal of Network and Computer Applications, November 2018.
- Ahmed Anwar, George Atia and Mina Guirguis "Towards a Protected Cloud Against Side Channel Attacks: A Game Theoretic Framework". In proceedings of of Allerton Conference on Communication, Control and Computing (Allerton), Monticello, IL, October 2018.
- Clara Novoa, Khan Siddique, Mina Guirguis and Alireza Tahsini. "A Game-Theoretic Two-Stage Stochastic
Programing Model to Protect CPS against Attacks". In proceedings of the IEEE International Conference on Industrial Informatics, Porto, Portugal, July 2018. [PDF]
- Ahmed Anwar, George Atia and Mina Guirguis."It’s Time to Migrate! A Game-Theoretic Framework for Protecting a Multi-tenant
Cloud against Collocation Attacks". In proceedings of the IEEE International Conference on Cloud Computing (CLOUD), San Francisco, CA, July 2018. [PDF]
- Noah Dunstatter, Mina Guirguis and Alireza Tahsini. "Allocating Security Analysts to Cyber Alerts Using Markov Games". In proceedings of the National Cyber Summit (NCS), Huntsville, AL, June 2018. [PDF]
- Mina Guirguis, Alireza Tahsini, Khan Siddique, Clara Novoa, Justin Moore, Christine Julien and Noah Dunstatter. "BLOC: A Game-Theoretic Approach to Orchestrate CPS against Cyber Attacks". In proceedings of the IEEE Conference on Communications and Network Security (CNS), Beijing , China, May 2018. [PDF]
- Ahmed Anwar, George Atia and Mina Guirguis. "Dynamic Game-Theoretic Defense Approach against Stealthy
Jamming Attacks in Wireless Networks". In proceedings of Allerton Conference on Communication, Control and Computing (Allerton), Monticello, IL, October 2017.
- Aaron Schlenker, Haifeng Xu, Mina Guirguis, Chris Kiekintveld, Arunesh Sinha, Milind Tambe, Solomon Sonya, Darryl Balderas, and Noah Dunstatter. "Don't Bury your Head in Warnings: A Game-Theoretic Approach for Intelligent Allocation of Cyber-security Alerts". In proceedings of the International Joint Conference on Artificial Intelligence (IJCAI), Melbourne, Australia, August 2017. [PDF]
- Aaron Schlenker, Haifeng Xu, Chris Kiekintveld, Arunesh Sinha, Milind Tambe, Mina Guirguis, Solomon Sonya, Darryl Balderas, and Noah Dunstatter. "Towards a Game-theoretic Framework for Intelligent Cyber-security Alert Allocation". In proceedings of the 3rd IJCAI workshop on Algorithmic Game Theory, Melbourne, Australia, August 2017.
- Terry Penner and Mina Guirguis. "Combating the Bandits in the Cloud: A Moving Target Defense Approach". In proceedings of the IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Madrid, Spain, May 2017. [PDF]
- Lavanya Tammineni and Mina Guirguis. "Toward Local Overlay-based Mobile Clouds". In proceedings of the Smart Cloud Networks and Systems Confercence (SCNS), Dubai UAE, December 2016.
- Ahmed Anwar, George Atia and Mina Guirguis. "Game Theoretic Defense Approach to Wireless Networks Against Stealthy Decoy Attacks". In proceedings of Allerton Conference on Communication, Control and Computing (Allerton), Monticello, IL, October 2016.
- Araceli Ortiz and Mina Guirguis. "Measuring the Impact of Unique Entry-Level Instructional Course Modules Designed to Inspire Computer Science Interest". In proceedings of the Annual ASEE Conference & Exposition, June 2016.
- Janiece Kelly, Mina Guirguis and George Atia "Pinball Attacks: Exploiting Channel Allocation in Wireless Networks". In proceedings of the IEEE ICC, Kuala Lumpur, Malaysia, May 2016. [PDF]
- Andrea Sciarrone, Igor Bisio, Fabio Lavagetto, Terrence Penner and Mina Guirguis "Context Awareness over Transient Clouds". In proceedings of the IEEE Globecom, San Diego, CA, December 2015.
- Andrea Sciarrone, Igor Bisio, Fabio Lavagetto, Terrence Penner and Mina Guirguis "Context-Awareness over Transient Cloud in D2D networks: Energy Performance Analysis and Evaluation". Transactions on Emerging Telecommunications Technologies, John Wiley & Sons Lt, November 2015.
- Ahmed Anwar, Janiece Kelly, George Atia, and Mina Guirguis "Stealthy Edge Decoy Attacks Against Dynamic Channel Assignment in Wireless Networks". In proceedings of the International Conference for Military Communications (Milcom), Tampa, FL, October 2015. [PDF]
- Heather Hinze, Mike Ruth and Mina Guirguis "Disrupting Adaptive Traffic Lights Cycles through Selective Jamming Attacks". In proceedings of the IEEE 81st Vehicular Technology Conference (VTC), Glasgow, UK, May 2015.
- Terry Penner, Alison Johnson, Brandon Van Slyke, Mina Guirguis and Qijun Gu "Demo: Transient Clouds". In proceedings of MobiCASE, Demo, Austin, TX, November 2014. [PDF]
- Vu Nguyen, Mina Guirguis and George Atia "A Framework for Identifying Stealthy Attacks on Mobile CPS Applications". In proceedings of Symposium on the Control of Network Systems (SCONES), Poster, Boston, MA, October 2014.
- Terry Penner, Alison Johnson, Brandon Van Slyke, Mina Guirguis and Qijun Gu "Transient Clouds: Assignment and Collaborative Execution of Tasks on Mobile Devices". In proceedings of IEEE Globecom, Austin, TX, December 2014. [PDF]
- Vu Nguyen, Mina Guirguis and George Atia "A Unifying Approach for the Identification of
Application-driven Stealthy Attacks on Mobile CPS". In proceedings of the 52nd Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, September 2014. [PDF]
- Qijun Gu and Mina Guirguis "Secure Mobile Cloud Computing and Security Issues". In K. Han, B. Choi and S. Song, High Performance Cloud Auditing and Applications, Chapter 3, Springer, New York, 2014.
- Terry Penner, Alison Johnson, Mina Guirguis and Qijun Gu "Transient Clouds: Assignment and Collaborative Execution of Tasks on Mobile Devices". Grace Hopper Conference, Poster Session, Minneapolis, MN, October 2013.
- Thomas Langford, Qijun Gu, Agustin Rivera-Longoria and Mina Guirguis "Collaborative Computing On-Demand: Harnessing Mobile Devices in Executing On-the-Fly Jobs ". In proceedings of the Tenth IEEE International Conference on Mobile Ad-hoc and Sensor Systems (MASS), ZheJiang, China, October 2013. [PDF]
- Trevor Hanz and Mina Guirguis "An Abstraction Layer for Controlling Heterogeneous Mobile Cyber-Physical Systems". In proceedings of the Ninth IEEE International Conference on Automation Science and Engineering (CASE), Madison, WI, August 2013.
- David Reynolds and Mina Guirguis "Control Theoretic Adaptive Monitoring Tools for the Android Platform ". In proceedings of the First IEEE International Workshop on Cloud Security Auditing, Santa Clara, CA, June 2013. [PDF]
- Mina Guirguis and George Atia "Stuck in Traffic (SiT) Attacks: A Framework for Identifying Stealthy Attacks that Cause Traffic Congestion". In proceedings of the IEEE 77th Vehicular Technology Conference (VTC), Dresden, Germany, June 2013.[arXiv version]
- Janiece Kelly, Seth Richter and Mina Guirguis "Stealthy Attacks on Pheromone Swarming". In proceedings of the IEEE International Multi-Disciplinary Conference on Cognitive Methods in Situation Awareness and Decision Support (CogSIMA), San Diego, CA February, 2013. [PDF]
- Emad Guirguis, Mina Guirguis and Nikhil Halkude "A Case for Low-level Jamming Attacks on Mobile CPS in Target Tracking Applications". In proceedings of the International Symposium on Pervasive Systems, Algorithms, and Networks, San Marcos, TX, December 2012.
Selected Presentations
- Combating the Bandits in the Cloud: A Moving Target Defense Approach
- CCGrid, Madrid, Spain, May 2017.
- A Unifying Framework for Identifying Stealthy Attacks
on Mobile CPS Applications
- University of Southern California, Teamcore, Los Angeles, CA, June 2016.
- University of Texas at Austin, El Paso, TX, June 2016.
- Old Dominion University, Norfolk, VA, December 2015.
- University of Central Florida, Orlando, FL, March 2015.
- Texas A&M University, College Station, TX, November 2014.
- UT Austin, Mobile and Pervasive Computing Group, Austin, TX, October 2014.
- Stealthy Attacks on Mobile Cyber-Physical Systems: Identifying Exploits on Coordination Methods between UAVs
- Air Force Research Laboratory, Rome, NY, July 2014.
- Transient Clouds: Assignment and Collaborative Execution of Tasks on Mobile Devices
- Grace Hopper, Minneapolis, MN, October 2013. [poster]
- Collaborative Computing in Mobile Clouds
- Air Force Research Laboratory, Rome, NY, July 2013.
- Stuck in Traffic (SiT) Attacks: A Framework for Identifying Stealthy Attacks that Cause Traffic Congestion
- IEEE 77th Vehicular Technology Conference (VTC), Dresden, Germany, June 2013. [slides]
- Securing Mobile Cyber-Physical Systems against Stealthy Attacks
- Industry Advisory Board (IAB) CS Meeting, San Marcos, TX, May 2012. [slides]
- NSF United-States/Middle-East Workshop On Trustworthiness in Emerging Distributed Systems and Networks, Istanbul, Turkey, June 2012. [slides]
- Air Force Research Laboratory, Rome, NY, July 2012. [slides]
- Secure and Trustworthy Cyberspace PI meeting, National Harbor, MD, November 2012 [poster]
- Stealthy Attacks on Pheromone Swarming Methods
- On Demand Computing With Mobile Devices
- UTSA College of Sciences Research Conference, San Antonio, TX, October 2012. [poster]
Lead PI
Collaborators (faculty members)
- George Atia (UCF)
- Christine Julien (UT Austin)
- Qijun Gu (Texas State)
Students
- Noah Dunstatter
- Alireza Tahsini
- Justin Moore
- Glen Stevenson
- Carter Ochsner
- Spencer Ginsburg
- David Crowe
- Khan Siddique
- Alex Tejada
- Darryl Balderas (graduated May'17 -- IBM)
- Emad Guirguis (graduated May'12 -- Intel)
- Daniel Haller (Summer'14 REU student - University of Maryland College Park)
- Trevor Hans (graduated May'13 -- UT Applied Research Laboratories)
- Hether Hinze (Summer'13 REU student - Texas State)
- Alison Johnson (Summer'13 REU student - Texas State)
- Janiece Kelly (graduated Dec'14 -- GM)
- Vu Nguyen (graduated Dec'14 -- GM)
- Terry Penner (graduated May'16 -- IBM)
- David Reynolds (graduated Dec'12 -- Microsoft)
- Seth Richter (Summer'12 REU student - LeTourneau University)
- Agustin Rivera (graduated December'13 -- General Motors)
- Sheryl Rosenthal (Summer'14 REU student - Texas State)
- Michael Ruth (Summer'13 REU student - University of Buffalo)
- Brandon Van Slyke (graduated May'14 -- IBM)
- Lavanya Tammineni (graduated Dec'16)
Hosted Seminars
- Christine Julien (UT Austin), "Gander: A Personalized Search Engine for the Here and Now", February 2012
- Dylan Shell (TAMU), "Multi-Robot Task Allocation Algorithms: Scale, uncertainty, and performance", September 2012
- Shouhuai Xu (UT San Antonio), "Cyber-Security Dynamics", September 2013
- Patrick Tague (CMU), "Toward Self-Managing, Context-Aware Networked Systems", October 2013
Mobile CPS (MCPS) Lab The MCPS lab consists of 8 iRobot Create robots, 2 SRV-1 Blackfin ones and 3 parrot drones. Various netbooks are mounted on the Create robots for control, vision and communication. Robots communicate with each other through servers (on which we implement our threat models). The lab also contains 8 Dell PowerEdge servers to run simulation and numerical analysis along with various desktop computers. Various laptops, sensors (MICAz) and Nexus devices are also available.
|
 |
Community Outreach
We host students from surrounding schools (elementary, middle and high school) into our lab. The goal of these visits is to expose the students to some of our ongoing research in the areas of robotics and sensor networks. The students will attend demonstration sessions prepared by our team.
If you would like to schedule a visit with your students to our lab, please contact Mina Guirguis by email: msg AT txstate DOT edu. |
Sponsors This project is sponsored by the National Science Foundation CNS CAREER award #1149397 |
 |